Modern malware is very “quiet” when it enters the network. Malware uses a number of evasive methods to remain undetected by cybersecurity tools.

Evasion techniques have become an important part of malware, so it’s important to know about effective countermeasures. In this article, we will cover the most widely used evasion method – sandbox bypass.
What are sandboxes and why does malware use workarounds against them?
A sandbox is an isolated and controlled virtual environment used to test and analyze suspicious incoming files that could potentially be malicious. After checking the files, they are allowed on the network.
The sandbox mimics systems running in a production environment to force malware to run as usual. Thus, they can be analyzed without malware affecting the actual production environment.
Malware developers equip their programs with features that allow them to identify that they are in a sandbox and bypass virtual environments to work only after they are allowed into the network.
Also read : What Is Sandbox,benefits Of Sandboxing Security
Typical Sandbox Evasion Techniques
Environmental assessment:
The malware first determines if it is in a virtual environment using the following system prompts:
- Register . If the registry shows an unusually low number of installed applications, it may indicate a sandbox environment.
- Hostname . Some sandboxes use specific hostnames or include specific characters in hostnames.
- The number of running processes . An unusually low number of running processes may indicate a sandbox environment.
- USB drives and printers . The presence of peripherals usually indicates an actual production environment.
- Hard disk size . Regular machines have a hard disk size of over 100 GB. An abnormally small disk size may indicate a sandbox.
- Screen resolution . It’s highly unlikely that anyone today will be working with a very low screen resolution (e.g. 800×600).
- Number of processors . Only virtual machines currently run on uniprocessor computers.
- RAM size . A small RAM size (for example, 1 GB) may indicate a sandbox.
- Sandbox agent . Some sandboxes are based on agents.
- Malware.exe _ For simplicity and convenience, many sandboxes change the name of the file being checked to something like “maleware.exe”. Many malware checks for malware.exe files as a sign of their presence in the sandbox.
If the result of these checks indicates the presence of a sandbox, the malware will simply not run and will wait until it passes the sandbox to run on the network.
User Interaction Detection:
Real production environments are usually characterized by user interactions such as mouse clicks, mouse movements, keystrokes, document scrolling, etc.
Some sandbox environments emulate user interaction to look like real production environments. However, some malware is smart enough to distinguish simulated behavior from real user interaction.
If the malware does not detect any user interaction or identifies user interactions as machine-generated (simulating an interaction), it will not execute.
Time Evasion:
Most sandboxes will not keep a file indefinitely, as this can impact performance if the file in question is part of a business process. In addition, sandboxes are resource intensive.
The malware will simply sit idle and wait for certain actions to take place, such as rebooting or logging in. Since these actions are not performed in isolated environments, the malware understands that it is online and activates.
How does Minerva use these malware evasion techniques?
Minerva’s Hostile Environment Simulation System (HES) is a layer between the OS and processes that completely controls how processes perceive their environment. With HES, malware’s evasion turns against itself, convincing it to “stay” in the sandbox forever, which is why it never deploys.
Many malware checks for malware.exe. In a normal system, a request for this file will result in a “file not found” system response, since most normal people do not have malware.exe files on their PC.

However, when Minerva is enabled, when a malware.exe file is requested, the platform intercepts the request and displays an imaginary malicious.exe file to the requester. The file does not actually exist, but Minerva pretends the existence of the process even if the file does not exist.

Whenever Minerva intercepts an evasion technique, a warning and an event is recorded on the platform’s dashboard, which can be analyzed later. This gives an idea of the attacks that have occurred, even if they have already been prevented at a very early stage.

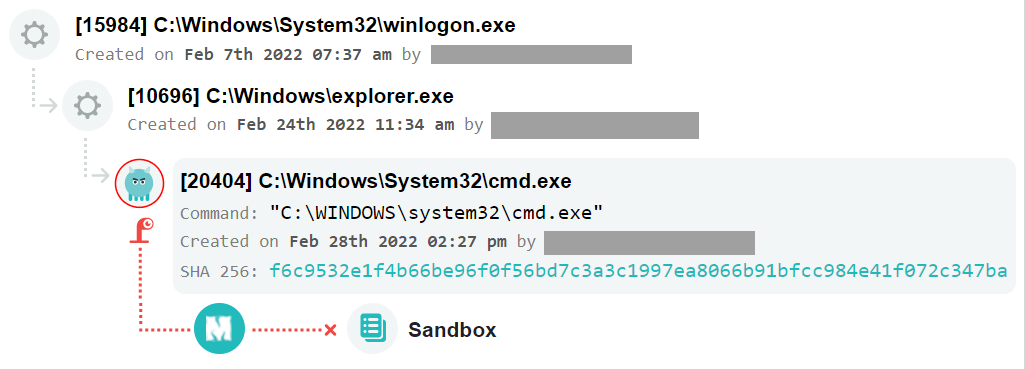
There are many more evasive techniques that Minerva protects against. If you want to try out this solution to protect your company, leave a request for a free pilot:
